Driving security transformation is becoming key; not justifying investments
The age-long debate around security metrics and dashboards seems very much alive within the CISO community. But it is often positioned in an outdated historical perspective.
For many CISOs, it seems to be still about “justifying investments” or articulating some form of “return on security investment”.
For CIOs and many other C-level executives, those ships sailed long ago. The large-scale cyberattacks and data breaches of the past decade, coupled with the change in privacy regulation they triggered, have put cyber risk on the Board’s agenda and the “When, Not If” paradigm resonates with many board members.
On security matters, “Tell me how much we need to spend” or “Are we spending enough” have become more common questions around the boardroom than “Why do you want to spend so much” …
So why are we still hearing some form of disconnect between the CISO and their bosses on the topic?
Trust is at the heart of the problem here, and the nature of the relationship between the CISO and their boss.
Many CIOs don’t have any problem justifying security investments in the face of non-stop cyberattacks. But they know as well that it is getting things done that will protect the firm, not just committing budgetary resources, so the CIO asking the CISO “show me what return we will get for such investment” is sometimes a way of saying something else:
- I don’t understand why you want to do this
- I am not sure this is the right thing to do
- I don’t think you will deliver it on any meaningful scale
It is often a challenge that is born out of some form of distrust. In our experience, where there is a complete and total commonality of views between the CISO and their boss around what needs to be done on security, and full trust around the execution of a common security roadmap, those issues don’t arise and the question of “return on security investments” is never asked.
The debate around security metrics – like the whole approach to building and managing a successful security practice – needs to shift from a short-termist project-driven approach, to a long-termist roadmap-driven one.
In such context, you mainly need metrics upstream, to build and sell the long-term security roadmap: Those have to be rooted in the reality of the challenges the firm is facing and backed against a sound appreciation of the threats it faces.
Security measures – and the associated investments they require – will protect the firm from real and active threats. Their implementation will modify the cyber risk, or cyber maturity, or cyber compliance posture of the organisation (depending on what the main drivers are at an executive level). That’s what the associated metrics need to capture and show.
They can be assessment-based metrics but need to be linkable to actual actions, and the methodology must reflect where necessary – in particular in relation to third-parties – the lack of availability or reliability of assessment data.
Visualisation is also a key factor: It is essential to put actions in the right long-term perspective, and to give management the sense that there is a real purpose behind security measures. This should be accompanied as well by the right governance and operating model, to give management assurance around the actual execution of the proposed roadmap.
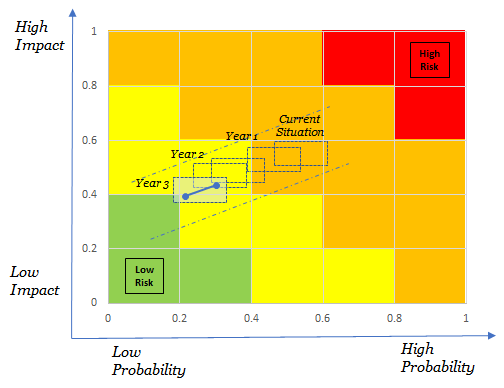
(In the example above, the size of each rectangle reflects the uncertainty around data availability or quality, and the evolution of the score for each year would have been associated to actual measures e.g. Year 1 = implementation of an Identity and Access Management model, Year 2 = implementation of a vendor risk management model, etc…)
You will also need metrics downstream, to show actual progress against the roadmap but those should be standard programme management metrics, and many large organisations will have well-established methodologies in place in support of that.
Overall, selling success will be key, and going back to the original scoring model used to build and sell the roadmap, will give senior executives a sense of continuity and management solidity.
Way beyond the justification of ad-hoc investments and pet-projects for the CISO, metrics have to be at the heart of the sound security practice, but they must be focused on tracking progress in time in support of a long-term transformative vision.
The Business Transformation Network has posted this article in partnership with Corix Partners.


