The same title often hides a large diversity of roles, positioned differently across their respective organisations. It often reflects the maturity of each firm towards the appreciation of the threats it faces, the need for business protection, and its appetite for controls.
For large groups, in particular where business units or geographies manage their own bottom line and have a significant degree of autonomy in real terms, it can result in a large population of security practitioners across the group with very diverse approaches, objectives and priorities.
Something that is increasingly a major source of concern in a world that is more and more “hyper-connected” and where data is the real “fuel” the business needs to burn on its journey towards digital transformation.
Often at the top is a Group CISO, but what could be their role in such context? And how to make it work?
Of course, security governance at group level cannot exist on its own, and somehow can only work if it follows broadly – and is embedded within – the governance model of the whole group.
As a result, the Group CISO will have to position their role based on 2 broad dimensions:
A sound appreciation of the real nature of the governance model at group level:
Some large groups operate very efficiently in a centralised model, driven by “command-and-control” principles, in which business units and geographies have a limited degree of real autonomy.
At the other end of the spectrum, and often in different industries, some large groups operate by influence in a very decentralised way, where business units and geographies have a large degree of real autonomy.
In between, a number of – more or less – dysfunctional models are quite common, many inspired by a strong distrust from Head Office and fuelled by internal politics and individual interests
A sound appreciation of the real need for group-wide business interaction:
Again, large groups are very diverse in these aspects. Many would have grown by acquisition over time in a more or less structured manner, and those different acquisitions might be at a different degree of integration.
It could be that historically the different parts of the group have always had little in common and therefore little interest in exchanging information or needs to integrate IT systems to operate.
Equally, it could be that the digital transformation is introducing the need for stronger cooperation across the group, as it opens up considerable competitive opportunities for cross-selling which could bring enormous growth (or indeed leave the group behind forever if they are missed, as competitors sail past).
Understanding these nuances is key for the Group CISO when positioning their role and its key objectives. They will be instinctive to a senior executive who might have spent years or decades in the organisation, but it could be much harder for a newcomer and could take time to grasp.
It is nevertheless a key step and it leads to 3 broad patterns in terms of role for the Group CISO, which we have already identified and analysed in earlier articles, focused on organisation and reporting lines:
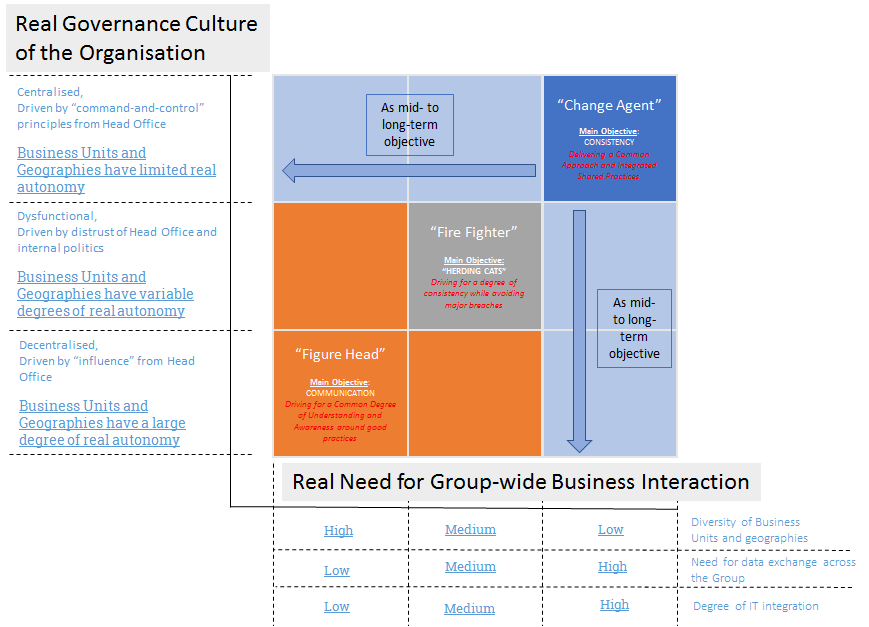
The Group CISO as a Figure Head
This is typical of large organisations where diversity is high and leaders lead primarily by influence. The prime objective of the Group CISO should be to communicate and drive a common degree of understanding and awareness amongst all stakeholder’s communities. There may also be an element of external representation to the role, within industry bodies, academia or similar groups.
The Group CISO as a Fire Fighter
This is typical of dysfunctional governance situations, and the prime objective of the Group CISO should be to drive – as much as possible – towards a degree of consistency in security practices across the group, while avoiding major breaches. This is by far the most complex role profile, and it will feel like “herding cats” most of the time for the Group CISO.
The Group CISO as a Change Agent
This is typical of situations where diversity is low and integration is high, with a strong “command-and-control” culture, but where security has never had a high degree of priority. The prime objective of the Group CISO should be to drive for consistency and the delivery of a common approach to security across the group, including shared integrated practices (such as a SOC for instance) where necessary.
How to drive action in all cases: Building a sense of community
In all cases, driving action, creating a sense of value around the Group CISO role and avoiding the “Ivory Tower” syndrome, will involve a number of key principles:
Create a clear mission statement for the Group CISO role, aimed at all security and business stakeholders across the group:
The role of the Group CISO cannot be vague, or difficult to read from the bottom up, or from the top down. But in particular, all security stakeholders across the group must have a clear idea of who the Group CISO is, what they do and why – even if the mandate coming top-down from executive management is not always that clear at their level.
Lead by listening:
The Group CISO function must bring something tangible to the various security stakeholders across the group. It is key to listen to them upfront to understand their constraints and their expectations. Ignoring those would kill trust and emphasize the idea of a Head Office “Ivory Tower” function. This is the most important part and often the hardest, as objectives, maturities and priorities across the group could vary enormously.
In return, build a clear plan with realistic expectations of delivery for all (at the level at which the group governance model allows you to work with realistic expectations of delivery):
It is key to have a clear security plan of action at a group level, in which each and every security stakeholder across the group fits and has a role to play with something clear and achievable for them to deliver. They need to have a sense of purpose and feel that collectively they achieve something for the group. This sense of community is the real key to success. In return, the Group CISO should leverage their influence at a group level to bring common resources and common budgets to the table that can help achieve common objectives and deliver work on common projects.
Bring all security stakeholders together at least once a year to keep contact, build trust and leverage on their skills and knowledge:
It could be an annual general event where they all come to report on progress and share achievements and issues. It could be several events per year with stronger thematics. In all cases, it is key to reinforce periodically a strong sense of community that transcends what may be happening around the security stakeholders in terms of management, governance or politics at their level, in their region, business unit or subsidiary. It is likely that many will find value in those exchanges, if anything at a human level, but also in terms of personal development and technical benchmarking. It can be sometimes a lonely role to be the CISO for a small division or a small region within a large group.
Across all those matters, the reporting line of the Group CISO will be important. As we pointed out above, the different role types overlap those identified in earlier articles: It should be at board-level and dictated by overall objectives for the role. But it’s only one aspect.
The personal profile of the Group CISO is essential: Many elements highlighted above call for a degree of seniority, gravitas and political acumen, as well as human qualities to listen to potentially very diverse people and bring them together.
Time is also a key factor as it could take 5 to 10 years to build a genuine security practice at group level in large firms, where nothing existed before. The Group CISO has to be prepared and rewarded to stay the course, and executive management above him has to be capable of working on mid to long-term objectives without deviating every time something happens internally or externally. Knee-jerk reactions on these matters just kill momentum and trust.
Success for the Group CISO role will come from working on all those fronts.
The Business Transformation Network has posted this article in partnership with Corix Partners.





