By Kelly White, Founder, RiskRecon, a Mastercard Company
The impact of a destructive ransomware attack extends far beyond the organization whose systems are encrypted. It harms all those who depend on the goods and services of the organization that criminals have taken offline.
Much has been written about hardening enterprises against the threat of ransomware, but what about protecting supply chains? Ideally, every supplier has a robust security program, strong ransomware defense, and stout resilience measures in place. Unfortunately, as we have learned in the face of other threats, this is not the case.
The reality of uneven cyber security strength in the supply chain leaves risk managers to answer critical questions for the enterprise. How susceptible is my supply chain to ransomware? Which of my hundreds of suppliers represent the greatest risk? What should I do to address the risks? Perhaps the most challenging dimension of all is that risk managers must manage supply chain risk with limited resources and the disadvantage of assessing suppliers from the outside.
Solving risk at scale requires good information upon which risk managers can build models and protocols for efficiently guiding their organizations to good risk positions. To that end, our research team has distilled five important insights for better managing supply chain ransomware risk based on an analysis of 633 publicly disclosed ransomware events occurring between 2017 and 2021.
- Do business with suppliers who have good cyber security hygiene; they have dramatically lower rates of destructive ransomware and data loss events.
- Revisit your supplier inherent risk ratings to include operational dependency; criminals are targeting every sector.
- Ensure that your suppliers have 24×7 ransomware protection, detection, and recovery operations; criminals are detonating ransomware seven days a week.
- Don’t assume recent victims of ransomware materially improve their cybersecurity program; the data shows they make only marginal improvement in their cybersecurity hygiene one year after an event.
- At the risk of stating the obvious, settle in for the long haul, the threat of ransomware is here to stay.
The Study
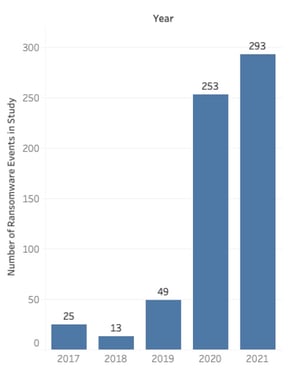 RiskRecon studied 633 publicly reported destructive ransomware events that occurred during the years 2017 through 2021. We did our best to include every publicly reported ransomware event for the years 2020 and 2021. The graph to the right shows the count of ransomware events distributed by year.
RiskRecon studied 633 publicly reported destructive ransomware events that occurred during the years 2017 through 2021. We did our best to include every publicly reported ransomware event for the years 2020 and 2021. The graph to the right shows the count of ransomware events distributed by year.
The benefit of limiting the study to publicly reported ransomware events, though excluding an untold number of unreported events, is that it inherently creates a population of events significant enough to be ‘newsworthy’. We further limited the ransomware events studied to only those that impacted operations due to encryption of systems. Events that only resulted in a data breach, though important, were not included. In this study, we are particularly keen on understanding events that result in material disruption to operations – a new dynamic that managers of supply chain risk have to solve.
For each ransomware event, RiskRecon documented essential facts, such as the exact date of detonation, the criminal gang responsible, the ransom paid, the victim’s industry and geography, and so forth. For each of the victim organizations, RiskRecon leveraged its continuous cybersecurity assessment and rating system to memorialize the cybersecurity hygiene at the time of the ransomware event. RiskRecon also analyzed the evolution of each organization’s cybersecurity hygiene in the months and years following the attack.
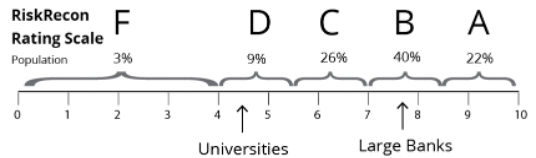
RiskRecon’s assessments are based on a passive assessment of nine security domains and 40 security criteria spanning thousands of security checks. RiskRecon’s assessment cover areas such as software patching, application security, web encryption, network filtering, and so forth. RiskRecon distills each assessment, detailing the IT profile, the security issues, and related severities, into a simple cybersecurity rating of A – F, with A being the best. The RiskRecon rating scale and the distribution of the total population of 100,000+ companies on which the model was built are shown below.
Click here to download the complete paper and get the full details on lessons learned from ransomware attacks.
About RiskRecon, a Mastercard Company
RiskRecon, a Mastercard Company, enables you to easily achieve better risk outcomes for your enterprise and your supply chain. RiskRecon’s cybersecurity ratings and assessments make it easy for you to understand and act on your risks, delivering accurate, risk prioritized action plans custom-tuned to match your risk priorities.
As a leading provider of cybersecurity ratings, RiskRecon continuously monitors the cybersecurity risk of over 15 million companies across even the most highly regulated industries from finance and insurance to aerospace and healthcare. RiskRecon provides deep, risk-contextualized, data-driven insights into the security risk performance across a customer’s entire ecosystem and helps pinpoint specific gaps in any organization’s security programs and performance. With a 99.1% accuracy rating of its data, as certified by a third-party, customers can confidently rely on RiskRecon’s data-driven insights.
Customers that leverage RiskRecon’s platform can transform traditional, manual methods of managing cyber risk into automated and streamlined processes – enabling them to build a highly efficient, scalable third-party risk management program. According to findings of the 2021 Total Economic Impact study conducted by Forrester Research, organizations using RiskRecon realize an average ROI of 147% over a three-year period.




